When I send email from Neoserra how can I have Neoserra authenticate on my behalf?
Unfortunately, email communications suffers from the fact that much unwanted mail is sent using spoofed addresses -- "spoofed" in this case means that the address is used without the permission of the domain owner. When you send a message from Neoserra to one or more clients, then you should know that Neoserra "spoofs" your normal email address. Basically, Neoserra makes it look like the message came from your domain name, when, in fact, it came from our outreachsystems.com domain. A lot of recipient mail servers will block your email from reaching your clients unless you tell the recipient mail servers that you allow such spoofing. You can do that by asking your IT department to implement the full DMARC policy.
If implementing DMARC is not an option, then Neoserra offers the "When sending email, have Neoserra authenticate on sender's behalf?" checkbox on the Administration|Configuration|General Settings page. Turning this option ON can provide the necessary permission for you to send email through the Neoserra servers:
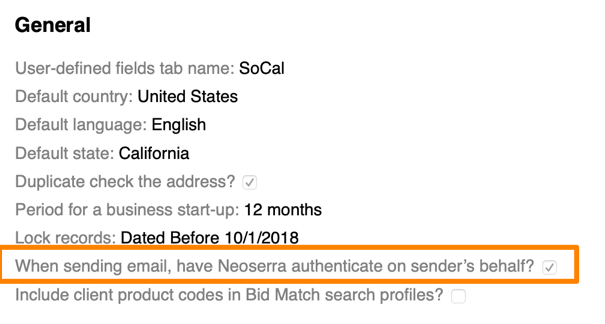
When this selection is activated, the following change is made:
- Emails sent from the Neoserra application will send at the SMTP protocol level: MAIL FROM: <sender+
@imail.outreachsystems.com> as discussed in this FAQ. All bounce-backs are routed to a vacuum application that logs the bounced message and records it in the Neoserra application. By logging the bounced message under the Administration|Email Operations Center the administrator will know which messages were not delivered. - The Neoserra application will use an OutreachSystems' controlled MTA that has a valid SPF record for sending email from the @outreachsystems.com domain.
Want more? Browse our extensive list of Neoserra FAQs.
